Data security has always been important to us at Borealis; in fact, it’s been one of our top priorities from the start, long before our clients had to worry about compliance with global privacy laws (like GDPR, CCPA and countless others). Recently, we’ve seen more and more emphasis on security. We’ve even received detailed questionnaires from prospects and clients who want to make sure our software complies with their standards.
This is entirely understandable, and we want you to know that we take your concerns seriously. Our clients rely on us to keep their sensitive stakeholder data safe at all times. To do just that, we chose hosting services that adhere to the highest industry standards for enterprise security (ISO 27001, SOC 1 Type II and SOC 2 Type II). Borealis software ensures the confidentiality, integrity, and availability of your stakeholder data to help you comply with all applicable data privacy laws. For example, we make sure that all your data is stored and maintained in the same region as the data center. This includes disaster recovery and data backups to ensure business continuity.
Constant improvements
We follow SaaS data security best practices. These begin with a dedicated in-house development team that constantly monitors the system, and end with external third parties that execute penetration tests and regularly check our system for vulnerabilities. We constantly evaluate security risks by carefully reviewing our customers’ IT assessments. This helps us to identify potential areas of improvement and proactively implement these changes even before they are asked.
If you are evaluating a cloud solution to manage your stakeholder engagement data, make sure your IT team is asking the software provider the right questions. If a vulnerability is detected, how quickly will they fix the problem? Will it take 2 weeks or 6 months? To ensure data security, this window should be as short as possible.
In 2023 we received our ISO 27001 certification, an internationally recognized standard that helps organizations manage information security to make information assets more secure. Organizations obtaining this certification implement strict security programs, assess risks, threats and vulnerabilities, and align with best practices. ISO 27001 certification demonstrates dedication to data protection, promoting confidence for customers and partners.
Here’s how our 15-plus years of SaaS development experience has helped us create a secure environment for your data.
Borealis’s 360 data security
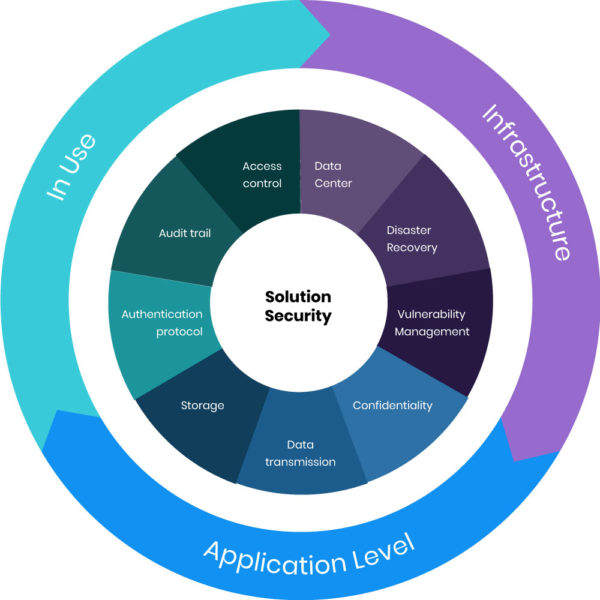
1. INFRASTRUCTURE SECURITY
Data center
Our infrastructure sits on high–availability servers with automatic failover capabilities which are hosted in Tier 3 certified data centers. These facilities are ISO 27001: 2005, SOC 1 type II (SSAE 16 and ISAE 3402) and SOC 2 type II compliant.
- Our redundant infrastructure allows you to continue working and accessing your data in Borealis even when we’re performing planned system maintenance and repairs.
- In case of a security incident, our team is immediately alerted and responds quickly to ensure your data remains secure and accessible.
- We carefully monitor and review all changes made to the infrastructure for legitimacy.
- We keep all security patches up to date to keep hackers out and to seal holes to risks like malware.
Disaster recovery
Your personalized instance of Borealis and all your data are mirrored in real-time at an off-site disaster recovery center. Should disaster strike, your data remains safe and accessible. In the extremely unlikely event that a physical server goes down, the virtual machines hosting the Borealis application will automatically replicate on another physical server to keep downtime to a minimum.
Vulnerability management
We use strict security practices to proactively test our infrastructure. This allows us to identify, prevent, mitigate, and classify vulnerabilities by:
- Monitoring technical systems and infrastructure 24/7.
- Scanning systems to automatically identify web application security risks.
- Using enterprise-grade firewalls and intrusion prevention & detection systems to protect the infrastructure against attacks that could interrupt service.
- Conducting third-party vulnerability intrusion tests to create an added layer of security.
2. APPLICATION SECURITY
Data confidentiality
We treat all client information with the utmost level of confidentiality. By default, all of your data is classified as confidential.
- All client data is encrypted according to the most up-to-date methods and access is limited to a need-to-know basis.
- All Borealis employees and consultants must adhere to contractual agreements governing data confidentiality and follow a yearly security awareness program.
- Our risk assessment methodology ensures that controls are in place and always working properly to protect client data.
- From our end, our team can only access your data on a need-to-know basis, such as when we need to monitor application health, perform maintenance, or when you contact us with a specific support request.
Encryption of transmitted and stored data
We encrypt all data according to cloud data encryption best practices to minimize the risk of breaches.
- All communications transmitted over the internet from within Borealis are encrypted using a high-grade cryptographic protocol.
- All data stored on Borealis’ servers are encrypted at rest by a high-quality SSL protocol.
- Encryption keys are securely stored.
- Individual user sessions are identified and re-verified with each transaction, using a unique token created at login for traceability.
3. DATA IN USE SECURITY
To provide our clients with a comprehensive security solution, we also safeguard data as it is actively moving through various parts of the infrastructure – whether it’s being created, updated, erased, or viewed from any device or workstation. This protects data from threats no matter where it is in the system, which is particularly important when BYOD policies are in effect.
Authentication protocol
For organizations that prefer to manage credentials at their end and have full connection control, Borealis supports several authentication protocols such as SAML, single sign-on (SSO), single logout (SLO), and lightweight directory access protocol (LDAP).
Audit trail
Data breaches have become a top concern for many businesses. Data privacy laws such as GDPR have made audit trails essential. These allow you to retain clear visibility over who did what and when in your Borealis platform – extremely helpful for compliance.
- All activities performed within Borealis are logged for full traceability, including changes to users or security settings.
- Downloads can be restricted, and all data exports are recorded as an activity along with the date and username.
User access controls
Borealis allows you to clearly define and fully control who has access to your data at your end. Document-level security ensures that everyone has easy access to the information they need while simultaneously safeguarding sensitive data.
- Only application administrators are allowed to create users and assign data security rules.
- All access is governed by strict password security policies with configurable complexity.
- Access controls can be assigned by project, campaign, communication, group, or role.
If you’re serious about keeping your stakeholder data safe, it’s time to get rid of spreadsheets and start working with stakeholder management software that keeps up with best practices in data security.
Download the Borealis Security Infokit for complete details.